PHP web application security and maintenance
Web security is an essential component of any business's web presence, and security considerations make up a big part of what I do as a developer and cloud consultant.
Businesses are often not aware of what their current web security posture is and how secure (or otherwise) their websites or applications are, particularly over time as a website ages while technology - and threats - move on.
Throughout my career as a PHP web developer, and now as a founder of the Manchester-based AWS consultancy, Si Novi, I've always had a keen focus on web security and have always enjoyed assisting businesses with improving their web security, ensuring data privacy and in bringing visibility of security into your compliance processes.
So what does my approach to web security look like? There are several considerations I make:
1. Keeping up with good practice security principles and web security news
I'm a firm believer in keeping up with current best practices and following authoritative sources on web security threats.
One of the best frameworks for considering web security is the OWASP foundation's top-10 security risks. This framework is the foundation of my security considerations, as it lists the current most dangerous and prevalent web security risks, together with example attacks and mitigations. The OWASP top-10 is updated every few years, keeping developers and businesses focused on the most serious threats.
I also keep up to date with the security features and best practice security techniques of the frameworks and applications I use, such as the Yii 2 PHP framework which itself takes web security very seriously.
Other good resources are the AWS Security Bulletins and the CVE Program.
2. Application architecture and DevOps security condiderations
Encryption in transit and at rest Management of keys, tokens, passwords Secure hashing of passwords using bcrypt HTTP security headers Testing for vulnreabilities Utilising a firewall such as AWS WAF3. Security and privacy by design and by default
I'm a keen proponent of cloud hosting and infrastructure, using secure cloud-based services like AWS S3 for encrypted document storage and utilising network-level security such as AWS Web Application Firewall.
These considerations should be made in terms of your responsibilties for personal data under DPA and GDPR, as under the GDPR, data protection should come as standard:
The GDPR requires you to put in place appropriate technical and organisational measures to implement the data protection principles and safeguard individual rights. This is ‘data protection by design and by default’.
In essence, this means you have to integrate or ‘bake in’ data protection into your processing activities and business practices, from the design stage right through the lifecycle.
3. Regular maintenance
Vehicles in the UK are subject to an annual legal health check - the MOT - and what's more, you have to replace the tires, brakes, oil and top up the washer fluid now and again to make sure your car is running properly, and safely.
I believe that it's essential that websites and web applications should be treated the same way, with regular periodic checks and maintenance to keep them up to date.
Open source web software by its very nature is regularly updated, often in response to newly discovered security threats - but without maintaining and updating a website, you won't benefit from these improvements and a site may become vulnerable.
The underlying operating systems and programming languages on which a website or application lives is also a constantly changing environment. For example PHP version 7 is now end-of-life and obsolete, yet I still see many sites running this old version of PHP. New versions of PHP or JavaScript libraries can often introduce incompatibilities into your own website or application code, which will require regular maintenance to resolve.
The more regularly a website or web application is maintained and updated, the more secure it will be, and the less effort and investment will be required in the long-term.
3. Using security tools
There are numerous excellent third-party tools available online to review the security of your website or web application. I like to build the use of these tools into my development, DevOps and website maintanence processes so that I always have a good picture of my current security posture.
Regular checks using these kind of tools is an important process can identify new threats or new opportunities to utilise technology to make your website or application more secure
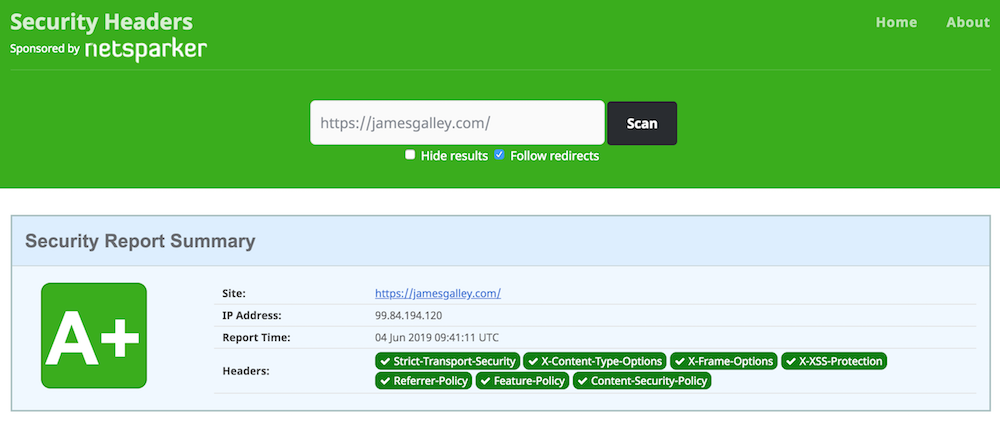
The excellent service securityheaders.com provides a score for your website's use of HTTP security headers. Configuring your website's security headers correctly can improve your resilience to attacks by giving you more control over what your website will allow users to do. Try testing your own site using securityheaders.com - if you see some red flags, contact me and we can work together to improve your security posture.


